From Global Reach to Local Rules
For the past decade, the promise of the cloud was its borderless nature. You could store data anywhere and access it everywhere. However, the rise of digital nationalism has fundamentally changed this dynamic. Governments are now enforcing strict mandates that require citizen data, financial records, and government secrets to remain on physical infrastructure located within their national boundaries. This shift turns location into a non-negotiable aspect of security strategy.
The financial magnitude of this shift is immense. The drive toward compliant, modernized infrastructure is fueling massive investment, with forecasts indicating that global IT spending reached a 30-year high in 2025. This isn't just about buying new hardware; it is about realigning technology with legal reality.
Organizations must now balance the need for compliance with the need for growth. While worldwide IT spending will total $5.43 trillion, a significant portion of this is directed toward systems that can respect these new borders. The days of treating the world as a single digital availability zone are over.
-
Data Residency: The physical location where data is stored.
-
Data Sovereignty: The concept that data is subject to the laws of the nation where it is physically located.
-
Data Localization: Laws requiring data to be created and stored within borders, often restricting cross-border transfers.
The GCC Banking Pivot
Consider a regional bank operating in Riyadh and Dubai. Previously, they might have used a general European data center for customer analytics to save costs. With Saudi Arabia’s Cloud First Policy and the UAE’s data protection laws, this is no longer viable for Personally Identifiable Information (PII). The bank now utilizes a "sovereign" zone provided by a hyperscaler within the Kingdom for customer records, while stripping anonymized data to send to a global public cloud for heavy AI processing. This split architecture satisfies the regulator without sacrificing the bank's ability to run advanced analytics.
Defining the Sovereign Cloud
Sovereign cloud is not merely a marketing term; it is an architectural and legal construct. It ensures that all data, including metadata, stays within a specific jurisdiction and prevents foreign access. For example, a US-based cloud provider operating a standard data center in Europe might still be subject to the US CLOUD Act, which could theoretically allow US authorities to access that data. A true sovereign cloud structure isolates the data legally and technically to prevent this extraterritorial reach.
The demand for this level of control is reshaping the market. We see this in the numbers, as cloud infrastructure spending reached $102.6 billion in Q3 2025. Much of this growth is driven by the expansion of regional data centers designed to meet local compliance needs.
For a digital enterprise operating in regulated sectors like healthcare or finance, sovereign cloud offers a shield. It guarantees that the infrastructure operator cannot move data to another region for backup or optimization without explicit consent, a common practice in standard public cloud agreements that often catches compliance officers off guard. To see how a unified managed security strategy is essential in these complex environments, explore Cloud Managed Security: Unified Security Strategy for Cloud and Hybrid Enviroinments.
Canadian Health Data Integrity
A healthcare provider in Ontario faces strict mandates under PHIPA (Personal Health Information Protection Act). They cannot risk patient records crossing into the United States. To solve this, they partnered with a managed service provider to implement corp it solutions that utilize a sovereign cloud node located physically in Toronto. This node is disconnected from the global control plane for sensitive tasks. The provider gets the scalability of modern virtualization but maintains the legal certainty of an on-premises data center.
The Hybrid Compromise for Mid-Market Firms
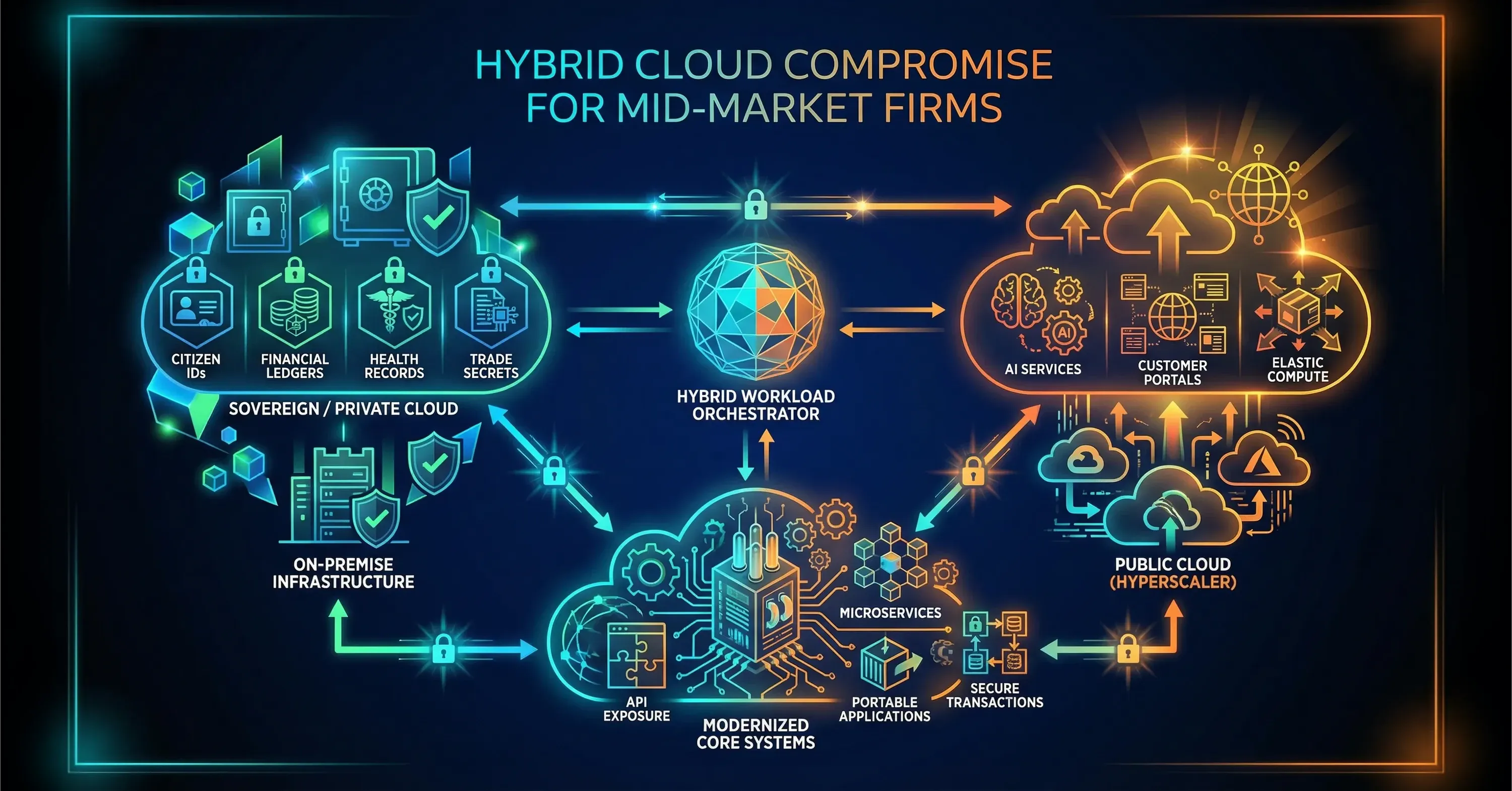
Completely exiting the global public cloud is rarely feasible or desirable. Hyperscalers like AWS and Microsoft Azure offer AI and machine learning tools that are difficult to replicate locally. The solution for most mid-market firms is a hybrid approach. This involves keeping "crown jewel" data - citizen IDs, financial ledgers, health records - in a sovereign environment while using the public cloud for less sensitive workloads.
This hybrid model requires significant IT modernization. Legacy systems often lack the flexibility to split workloads between different environments. Companies are recognizing this gap, and as a result, enterprises are dedicating 25–30% of IT budgets to infrastructure modernization. This investment goes toward updating applications so they can be "portable," allowing them to move between sovereign and public clouds as regulations or business needs dictate.
This modernization often involves revisiting the oldest and most reliable parts of the IT stack. Surprisingly, the mainframe is playing a central role in this new hybrid world. Recent data shows that mainframe modernization project ROI has surged between 288% and 362% in 2025. By connecting these secure, transaction-heavy systems to modern cloud interfaces, companies can keep core data secure on-premise (the ultimate sovereign cloud) while exposing services to the web.
To ensure secure and compliant modernization, organizations can look at practices outlined in Balancing Cloud Computing and Cloud Security: Best Practices.
-
Assess Data Classification: strict auditing of what is "secret" vs. "public."
-
Update Connectivity: ensuring low-latency links between sovereign and public nodes.
-
Review Legal Contracts: verifying that your provider indemnifies you against data residency breaches.
Retail Logistics
A large logistics firm uses a hybrid model to manage its supply chain. The core inventory database, which includes pricing strategies and supplier contracts, resides on a private, sovereign cloud to protect trade secrets and comply with local trade laws. However, the customer-facing tracking portal runs on a global public cloud to ensure fast load times for users worldwide. The two systems talk via secure, encrypted APIs, ensuring that only necessary tracking numbers - not sensitive pricing data - leave the sovereign environment.
Overcoming Transformation Fatigue
Navigating these complex architectures is exhausting for internal IT teams. The constant pressure to adopt new technologies while adhering to shifting regulations has led to burnout. In fact, 50% of respondents report experiencing “transformation fatigue”. When teams are tired, they make security mistakes, which is a dangerous prospect when dealing with data sovereignty.
To combat this, many CIOs are turning to external partners. Rather than building sovereign capabilities in-house, they lean on specialized firms. A leading provider of managed IT services can offer the necessary corp it solutions - from cybersecurity frameworks to infrastructure management - that bridge the gap between compliance and capability. For strategies to avoid the pitfalls of patchwork, siloed IT tools, see The Danger of the 'Franken-Stack': Why Patchwork IT Will Kill Your Growth and How to Build a Secure, Scalable Foundation.
The reliance on outside expertise is becoming the norm. It is noted that 81% of companies intend to rely more on consultants for technology upgrades. These partners help navigate the specific nuances of local laws, ensuring that a "sovereign" solution in Dubai meets the specific criteria of the UAE government, which might differ from what qualifies as sovereign in Germany or Canada.
Government Agency Partnership
A government agency tasked with digitizing citizen records faced a skills gap. Their internal team understood legacy databases but lacked experience with modern cloud orchestration. By bringing in external consultants, they executed a migration to a government-approved sovereign cloud. The partners handled the architectural complexity and compliance mapping, allowing the internal staff to focus on service delivery rather than infrastructure plumbing. This prevented project stall and ensured the agency met its legislative deadline for digitization.
What Is Sovereign Cloud?
Sovereign Cloud is a cloud computing architecture designed to deliver data access and storage in compliance with the local laws and regulations of a specific country or region. Unlike standard public cloud services, where data may be replicated across global borders for efficiency, sovereign cloud ensures that all data - including metadata, authentication credentials, and user content - remains resident within the legal jurisdiction. It safeguards organizations from foreign legislative access requests, such as the US CLOUD Act, making it essential for government entities, financial institutions, and highly regulated industries.
Conclusion
The era of the "borderless" cloud has evolved into the era of the "jurisdictional" cloud. For leaders in finance, government, and healthcare, the physical and legal location of data is now a primary design constraint. By leveraging hybrid architectures and modern corp it solutions, organizations can navigate this complex landscape.
Whether you are operating under the strict privacy mandates of Canada or the ambitious digital policies of Saudi Arabia, the goal remains the same: complete control over your digital assets. The sovereignty shift is not just a compliance hurdle; it is an opportunity to build a more resilient, trustworthy, and secure digital enterprise that is ready for the realities of 2026.
Related Reading: