What You’ll Learn
You’ll learn how a unified core for email, collaboration, and storage closes blind spots, how modern endpoint protection and SSO block most threats, and how cloud-native disaster recovery gets you back online in minutes. We’ll also show where technology business solutions provide ongoing optimization so your team can focus on growth.
Why Do SMBs End Up With a Franken-Stack?
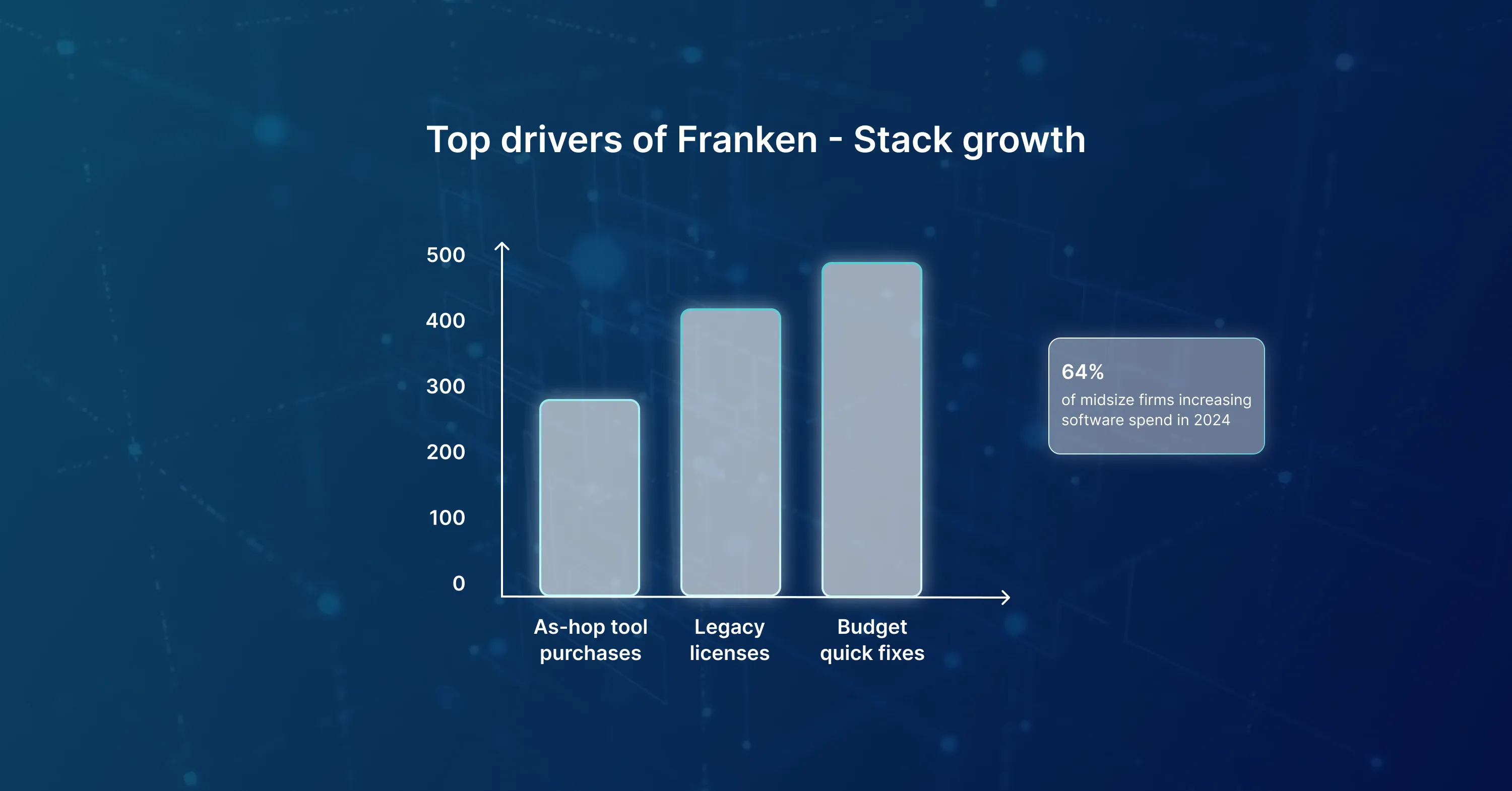
Most Franken-Stacks form slowly. A department grabs a SaaS trial, another installs an on-prem server from a past era, and soon nobody remembers who owns what.
- New hires buy “just one” tool to finish a project
- Legacy licenses keep rolling because canceling feels risky
- Budget cycles favor quick fixes over long-term strategy
A recent 2025 survey shows 64% of midsize companies will boost software spend in 2024. Spending without a plan only makes the stack bigger.
The takeaway: growth amplifies the mess unless you set a clear foundation. For a modern blueprint on how cloud-first strategies and elastic architectures can replace this legacy approach, explore Cloud Services and DevOps.
Hidden Costs and Risks: Compliance, Security, and Lost Productivity
Adding another point solution may feel cheap, but the real bill shows up later.
- Compliance gaps: Old email servers rarely meet GDPR or HIPAA logging rules
- Security holes: 29% of enterprises list cyber threats as a top fear, according to Gartner
- Lost hours: Switching between six interfaces can waste 5–10 minutes per task
Each forgotten plug-in is a door for attackers. When an audit hits, piecing logs across multiple apps can take days. Staff frustration rises, turnover follows, and growth stalls.
Bottom line: the patchwork costs more than ripping it out and rebuilding. To explore proactive security strategies, continuous monitoring, and predictable cloud maintenance, see Information Security.
Building a Unified Backbone: Email, Collaboration, and File Storage
A solid core platform replaces scattered shares and endless forwarding chains. Think Microsoft 365 or Google Workspace, both packed with enterprise software grade controls.
Key Benefits
- One admin console to set retention, MFA, and region rules
- Real-time coauthoring eliminates version chaos
- Tiered access makes client data isolation simple
A leading provider of Managed IT Services can migrate mailboxes and drives with minimal downtime, then enforce automatic backups. With a single pane of glass, your team works faster and auditors smile.
The lesson: start with the backbone, everything else plugs in cleanly later.
Modern Endpoint Protection and Single Sign-On: A One-Two Security Punch
Every laptop, phone, or browser tab is a potential breach point. Advanced agents powered by AI spot abnormal behavior in seconds.
What Modern Protection Looks Like
- AI-driven malware detection that learns locally
- Device encryption tied to cloud keys
- Automated patching windows outside work hours
Pair that with SSO and users log in once to reach email, ERP, and automation tools. You cut credential fatigue and slash phishing success rates.
Transitioning from five passwords per user to one secure identity sounds small but is massive: fewer reset tickets, tighter logs, and instant off-boarding when someone leaves.
For best practices on embedding security, compliance by design, and cloud-native protection into your stack, review Information Security services.
Right-Sizing and Ongoing Support: Managed Services That Grow With You
A common fear is overpaying for cloud capacity. Skilled partners watch usage trends and tune instances monthly.
- Auto-scaling rules keep compute in line with real demand
- Reserved pricing locks discounts for predictable workloads
- Quarterly reports flag unused licenses, saving real cash
Large firms see only 31% of expected revenue lift from digital projects, notes McKinsey research. Expert guidance ensures you are not part of that statistic.
The point: technology business solutions are not “set and forget.” Continuous care squeezes every dollar from your stack. For more detail on optimizing resources and managed support, visit Managed IT Services.
Disaster Recovery in Minutes, Not Days
Old tapes and on-prem backup appliances fail when the office floods. Cloud-native recovery spins workloads up in a different zone almost instantly.
Must-Have Elements
- Immutable snapshots every 15 minutes
- Cross-region replication
- Run-book automation that rebuilds networks and firewalls on launch
In a live drill, teams with this setup regained full operations in under 20 minutes. Compare that to legacy restores that can stretch into multi-day outages. Revenue saved often pays for the service many times over.
A robust disaster recovery plan and regular incident drills are hallmarks of Managed IT Services, ensuring your environment stays resilient and recoverable at all times.
How to Start Replacing the Patchwork Today
Change feels heavy, but a phased approach works.
- Map every tool, license, and shadow IT account
- Set security and compliance goals, then pick a backbone platform
- Migrate email and storage first, with limited pilot users
- Roll out SSO and endpoint agents company-wide
- Decommission redundant apps and shift funds to continuous support
- Test disaster recovery quarterly, tune, and document
Automation tools built into modern suites speed each step. Celebrate small wins; momentum matters.
Conclusion
A Franken-Stack feels harmless until a breach, audit failure, or outage hits, then the real price reveals itself. Building on a unified, secure foundation backed by modern endpoint defenses, smart automation, enterprise software controls, and rock-solid disaster recovery turns IT from a risk into an advantage. Your people work faster, your data stays safe, and growth is no longer held back by yesterday’s patchwork.