Stop Buying Security Tools. Start Buying Security Outcomes
This article unpacks why the “as-a-service” delivery model is overtaking appliance and on-prem setups. You’ll see how SaaS-based security aligns with a modern cloud security model, relieves alert fatigue, and converts fixed capital outlays into measurable resilience.
We’ll finish with a practical roadmap for evaluating managed threat detection partners and budgeting for business continuity rather than yet another box.
The hidden cost of chasing tools
Chasing the latest shiny tool feels proactive, yet the hidden downsides add up.
- Integration headaches: mismatched APIs and half-finished workflows
- Alert floods: thousands of low-value notifications that bury true incidents
- Shelfware: licenses bought “just in case” but never enabled
- Talent drain: scarce analysts stuck maintaining infrastructure instead of hunting threats
Gartner projects global cybersecurity spending will hit $213 billion in 2025 research shows. Still, breach numbers keep climbing. The message is clear: tool volume does not equal protection.
Understanding these inefficiencies sets the stage for a delivery model that fixes them at the root.
A quick reality check
Security leaders report that only 20 % of alerts receive human review before dismissal, and most SIEM deployments absorb 40 % of the security budget yet produce little actionable insight. Double-spending and under-monitoring coexist in the same environment. There has to be a better way, and there is.
The next section defines it.
What is Security as a Service?
Security as a Service (SECaaS) delivers core defense functions - prevention, detection, response, and compliance - through cloud-hosted platforms run by specialized providers. Customers subscribe to security outcomes, freeing them from the cost and complexity of operational overhead.
- Subscription model: monthly or annual fees cover software, infrastructure, and expert staffing
- Cloud delivery: services live in a hardened multitenant platform that aligns with your cloud security model and on-prem assets alike
- Outcome SLAs: metrics focus on dwell time, mean time to detect, and incident closure, rather than CPU cores or log capacity
Instead of provisioning servers and tuning rules, organizations plug into continuously updated analytics and threat intel curated by the provider. Think Netflix for cyber defense - always on, always current.
Service categories at a glance
- Managed threat detection and response (MDR)
- Security operations center as a service (SOCaaS)
- Email, web, and endpoint protection
- Identity and access management
- Compliance reporting and governance
Each category removes infrastructure burdens and hands you expert capabilities from day one. For a broader perspective on solutions that support these functions, review our Information Security offering.
By decoupling security from physical appliances, SECaaS mirrors the consumption pattern that already revolutionized CRM and accounting. Why should defense lag behind?
How SaaS-based defenses outperform traditional models
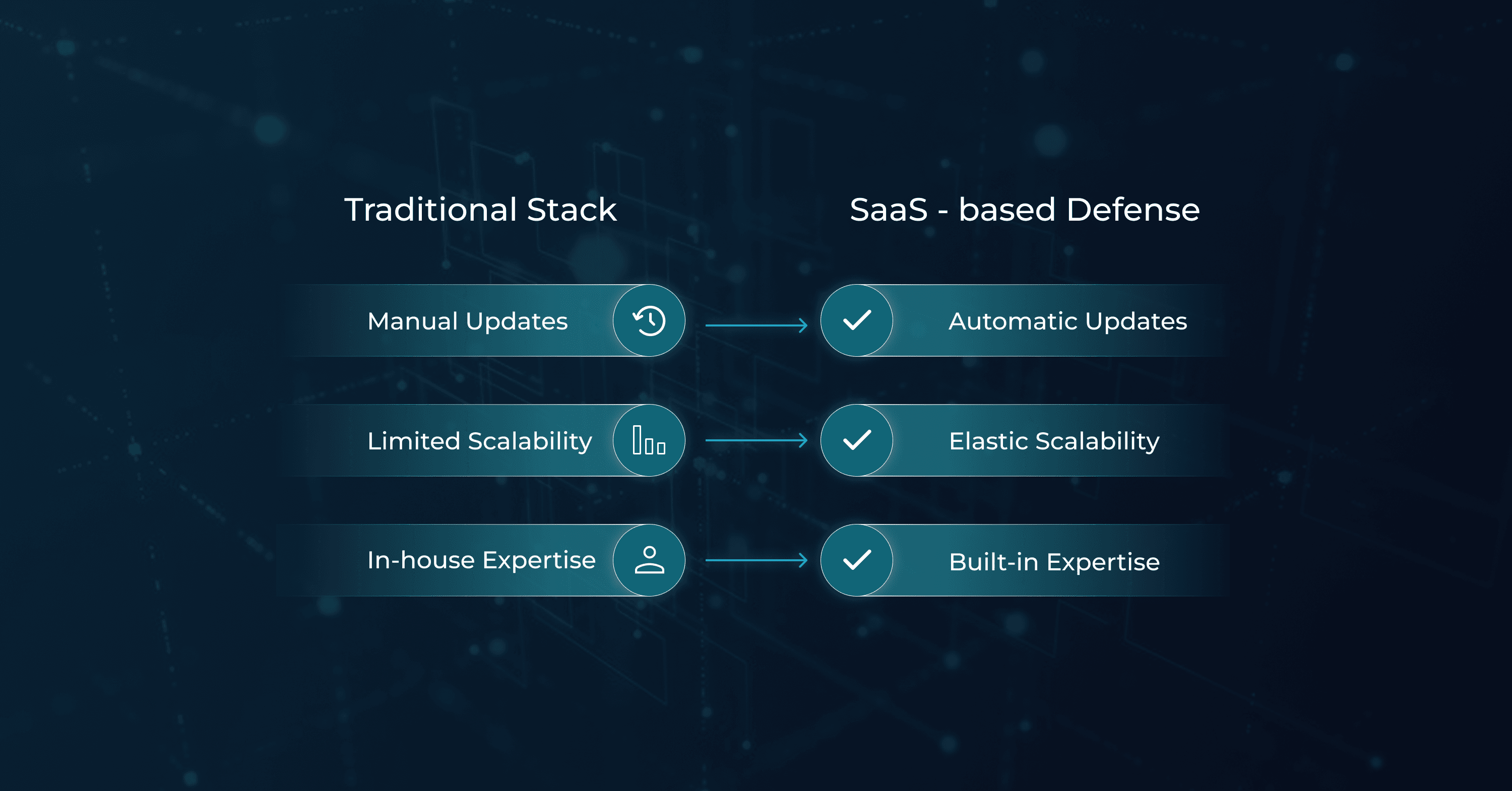
Upgrading to as-a-service is not a technology swap, it is a strategic pivot. Let us see why.
Continuous improvement baked in
Traditional stacks receive major updates quarterly at best. SECaaS providers roll out detections and heuristics daily or even hourly, informed by telemetry across their customer base.
- Zero-day coverage arrives automatically
- Machine learning models refine themselves on live global data
- Customers benefit from network effects that point products cannot match
Elastic scale minus the bills
Cloud breaches do not schedule appointments. When an incident spikes log volume tenfold, SaaS platforms expand storage and compute instantly, then shrink when the storm passes. No one issues a purchase order, and you pay only for the burst you used.
Human expertise on tap
Even a well-funded SOC struggles to hire reverse engineers, threat hunters, and forensic analysts. SECaaS subscriptions bundle those experts.
- 24×7 monitoring
- Multi-language, multi-region coverage
- War-room support during active incidents
A leading provider of Managed IT Services, offering comprehensive solutions for infrastructure management, cloud computing, and cybersecurity, often embeds elite responders directly into its service tiers, cutting down crisis response time.
Proven results
Research firm Persistence Market Research estimates the global Security-as-a-Service (SECaaS) market will reach US $16.4 billion in 2025, and project it to grow at a CAGR of 15.7 % to reach about US $45.4 billion by 2032
By the end of this section, the takeaway is simple: SaaS defenses adapt faster, scale smoother, and include skill sets you cannot hire fast enough.
Counting the dollars: cost efficiency in plain numbers
Security budgets rarely keep pace with risks. Here is how SECaaS stretches every dollar.
- Shifts capital expense to operating expense
- Bundles tooling, hosting, and labor in one line item
- Reduces maintenance overhead by up to 70 % according to internal case studies
- Shrinks mean time to detect, which directly lowers breach impact
Allied Market Research estimates the market will hit $75 billion by 2032 on 19.4 % annual growth studies show, driven largely by cost predictability. Finance teams like predictable spends, and CISOs like pay-for-what-you-use agility.
The math is compelling: instead of buying six different tools, one managed threat detection subscription covers them with better outcomes. For organizations exploring cost optimization and shifting to cloud models, our Cloud Services and DevOps page highlights additional advantages.
From products to business resilience: budgeting for outcomes
The pivot from tool acquisition to risk reduction requires a mindset shift across leadership.
Begin by reframing your budget conversation:
- Replace line items like “next-gen firewall renewal” with “reduce ransomware dwell time to under 30 minutes.”
- Map each business service - ecommerce checkout, SaaS login, ERP - to the security controls that protect revenue flow.
- Ask vendors to quote outcome-based SLAs, not just throughput numbers.
When board meetings focus on resilience metrics, funding aligns itself automatically. Tools become a means, not the end.
Align with the cloud security model
Most organizations already run workloads in AWS, Azure, or Google Cloud. SECaaS extends the shared responsibility model. The provider secures the layers you cannot reach alone, while you maintain configuration hygiene and identity permissions. This clarity reduces finger-pointing and audit friction.
A second mention of that leading managed IT services partner fits here: organizations working with such integrators often bundle SECaaS with broader cloud optimization projects, trimming total IT cost by double digits. To see how such integrated solutions can drive business value, you might explore our broader Services portfolio.
By now, the reader should see that budgeting outcomes de-emphasizes hardware refresh cycles and stresses uninterrupted service delivery instead.
Choosing the right SecaaS provider
Not all providers deliver the same value. Use the checklist below when evaluating vendors.
- 24×7 monitoring with less than 15-minute response SLA
- Native support for multi-cloud and on-prem logs
- Transparent pricing with no data overage penalties
- Ability to integrate with your ticketing and SOAR tools
- Clear ownership boundaries in the incident lifecycle
Red flags to watch
- “Black box” analytics that hide detection logic
- Long-term contracts with steep exit fees
- Overreliance on automation without human review
Selecting wisely ensures the promise of security as a services becomes reality, not another budget line that disappoints.
At this point, you know how to shift from tool fatigue to outcome certainty by partnering with a team that lives and breathes threat detection.
Security outcomes beat tool ownership every time.
Conclusion
Tool sprawl, alert fatigue, and ballooning budgets prove that piling on products does not guarantee safety. Security as a Service trades hardware and licenses for measurable resilience powered by elastic cloud platforms and seasoned analysts. The result: better protection, predictable costs, and a security program that keeps pace with the business, not the other way around.