What You’ll Learn
Over the next few minutes you will see how three pillars - continuous monitoring and predictive cloud maintenance, rapid response with thorough recovery, and security baked into every commit - form a safety net for SaaS, FinTech, E-commerce, HealthTech, and Media workloads. You will also discover how Continuous Delivery (CD), Infrastructure as Code (IaC), and DevSecOps make 24/7 operations repeatable and cost-effective.
The High Stakes of Always-On Services
Customers expect a checkout page to load in milliseconds and a telehealth session to stay stable through an entire exam. Cloud outages turn those expectations into public support tickets and social media rants.
Those numbers show that companies are pouring resources into uptime guarantees rather than accepting outages as “normal.” The following pillars explain how.
What Is Cloud Support?
Cloud support is the combination of 24/7 monitoring, predictive maintenance, rapid incident response, and ongoing security hardening that keeps cloud workloads healthy, performant, and safe while freeing internal teams to focus on innovation. Discover more about our Cloud Services and DevOps offerings.
Pillar 1: Continuous Monitoring and Predictive Cloud Maintenance
Invisible issues create the loudest outages. A smart monitoring stack shines light on them before users notice.
- Metrics: CPU, memory, disk I/O, latency, error rates
- Tracing: request path across microservices
- Logging: structured, aggregated, searchable in real time
- Synthetic checks: simulate user flows every minute
Why predictive beats reactive
Traditional alerting shouts when a threshold is breached. Predictive analytics, powered by machine learning on historical data, whispers before things get critical.
Benefits
- Fewer false positives because models learn normal baseline
- Maintenance windows can be scheduled, avoiding user impact
- Capacity planning becomes evidence based, cutting over-provisioning costs
Tools and Metrics to Watch
Popular choices include Prometheus, Grafana, AWS CloudWatch, Azure Monitor, and Google Cloud Operations Suite. Add custom business metrics - cart abandonment, video rebuffer rate - to align alerts with revenue.
A leading provider of Managed IT Services often bundles these tools, delivering dashboards that blend system health and business KPIs into a single cockpit.
Continuous monitoring plus predictive cloud maintenance means you rarely get surprised by a 2 a.m. pager. Instead, you adjust course during daylight hours.
Pillar 2: Rapid Response and Service Restoration
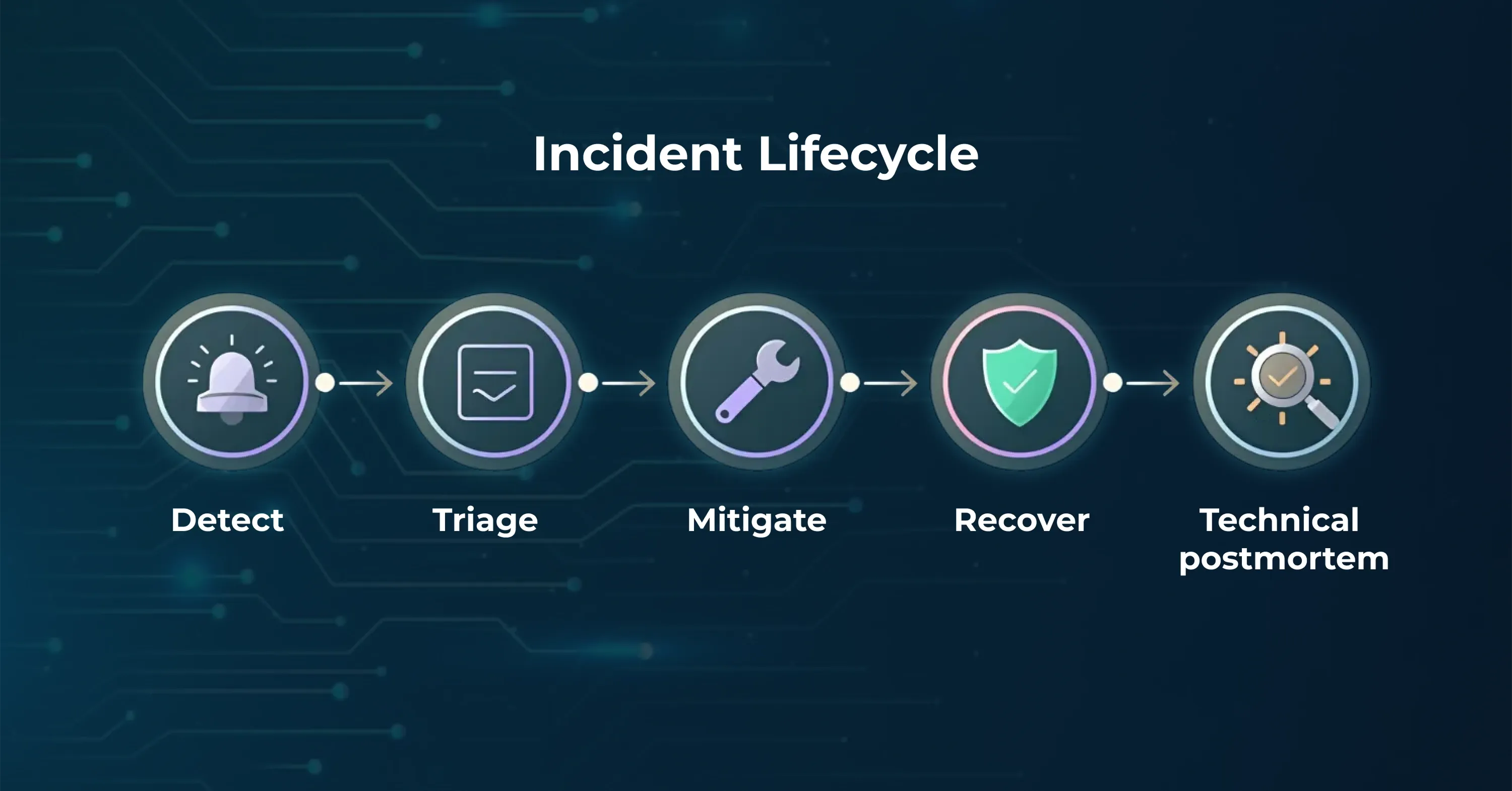
Even with stellar monitoring, incidents will strike. What separates leaders from laggards is the speed and clarity of their response.
Core components
- Incident playbooks: step-by-step actions for the first 15 minutes
- Auto-healing: health checks that restart unhealthy pods or VMs
- Disaster recovery plans: clearly documented RTO/RPO targets
- Immutable backups: daily snapshots pushed to a different region
- Blameless postmortems: focus on the fix, not finger-pointing
Disaster Recovery, Backup, and Root Cause Analysis
Backup frequency and retention rules must suit data sensitivity - finance logs differ from media assets. Automated restores are rehearsed quarterly so everyone knows the drill.
Root Cause Analysis (RCA) digs below the surface:
- Gather logs, metrics, timelines.
- Identify the primary failure and any contributing factors.
- Recommend code, config, or process changes.
- Share findings across teams for collective learning.
Wrapping up: Rapid response backed by repeatable DR and RCA shrinks mean-time-to-restore (MTTR) and converts painful lessons into stronger architecture. For end-to-end guidance, explore our Services.
Pillar 3: Security Through DevSecOps and Regular Patching
Security lapses can be more damaging than downtime. DevSecOps threads safety checks throughout the delivery pipeline, catching misconfigurations and vulnerable libraries early.
Key practices
- Shift-left scanning of Infrastructure as Code templates
- Container image signing and vulnerability scanning
- Automated security tests in CI/CD
- Weekly patching cycles for OS and middleware
- Least-privilege IAM policies with short-lived tokens
Regulatory-heavy sectors such as HealthTech and FinTech see added peace of mind. Continuous compliance reports satisfy auditors without manual spreadsheet marathons.
Takeaway: A strong security posture is not a side project. It is an everyday discipline that guards the uptime you work so hard to protect. See how Information Security services can help you stay secure.
Continuous Delivery and IaC: The Engine Behind 24/7 Changes
High availability is pointless if code deploys are painful. CD pipelines built on IaC make shipping safe and boring.
From Commit to Production Without the Drama
- Developers push code to Git.
- CI runs unit, integration, and security tests.
- Approved builds trigger IaC tools like Terraform or AWS CloudFormation.
- Blue/green or canary releases shift traffic gradually, limiting blast radius.
- Rollbacks are a single command: the previous version still exists.
Because environments are defined in code, you can recreate them in minutes. This repeatability underpins 24/7 operations - no more weekend change freezes.
Final note: CD plus IaC turns infrastructure into a version-controlled asset, not a snowflake nobody dares to touch. To learn more, visit Cloud Services and DevOps.
Choosing a Partner for Cloud Support and Technical Support Services
Most organizations lack the bandwidth to staff round-the-clock rotations. External technical support services fill the gap.
Selection checklist
- Proven SRE track record with similar workloads
- Transparent SLAs: sub-5 minute response, defined escalation path
- Tooling compatibility with your stack
- Security certifications (ISO 27001, SOC 2)
- Cultural fit: responders communicate clearly, own problems through resolution
A leading provider of managed IT services, offering comprehensive solutions for infrastructure management, cloud computing, and cybersecurity, meets those benchmarks while letting your engineers focus on product features.
The right partner extends your team, not replaces it, keeping uptime high and stress low. To see how we help businesses across sectors, check our Industries expertise.
Conclusion
Downtime is inevitable - but chaos isn’t. Managed DevOps transforms those tense 2 a.m. alerts into calm, predictable recoveries. By combining continuous monitoring, rapid restoration, and built-in security, your infrastructure stops being a liability and becomes a launchpad for innovation.
This is the shift from firefighting to foresight - where every patch, backup, and deployment is automated, tested, and trusted. Your team can finally focus on building what matters while experts keep your cloud always-on, secure, and ready for whatever comes next.